Adobe Flash Player updates available for OS X on September 10, 2013
Adobe Flash Player updates are available that address a recently-identified Adobe Flash Player web plug-in vulnerability.
When attempting to view Flash content in Safari, you may see this alert: "Blocked Plug-in".
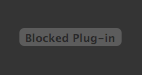
Selecting it will display this alert:
"Adobe Flash Player" is out of date.

- Click "Download Flash…" and Safari will open the Adobe Flash Player installer website.
- Click the "Download now" button to download the latest Adobe Flash Player installer.
- Open the downloaded disk image.
- Open the installer and follow the onscreen instructions.
Additional Product Support Information

 Twitter
Twitter Facebook
Facebook